Advanced Computer Networks Important Unit 1 & 2
ETIT401
Q1 Short Answer Questions.
a. What is the purpose of Reverse Address Resolution Protocol (RARP)?The purpose of Reverse Address Resolution Protocol (RARP) is to obtain an IP address from a physical address. It is used by a device to discover its IP address when it knows only its physical (MAC) address.
b. What is congestion control?
Congestion control is the set of mechanisms used to avoid or alleviate congestion in a network. It is used to manage the amount of data being sent over a network in order to prevent network congestion, which can lead to dropped packets, increased latency, and decreased throughput.
c. What is Protocol Independent Multicast (PIM)?
Protocol Independent Multicast (PIM) is a multicast routing protocol that is designed to work with any unicast routing protocol. PIM is used to distribute multicast traffic in a network, enabling a single multicast source to transmit data to multiple receivers.
d. Difference between connection less services and connection oriented services?
Connectionless services and connection-oriented services are two types of network communication services. Connectionless services do not require a dedicated connection between sender and receiver, and each packet is treated independently. Connection-oriented services require a dedicated connection between sender and receiver, and a connection is established before data transmission begins.
e. What is Distance Vector Multicast Routing Protocol (DVMRP)?
Distance Vector Multicast Routing Protocol (DVMRP) is a multicast routing protocol that is based on the distance vector algorithm. It is used to distribute multicast traffic in a network by propagating multicast packets to all nodes in a network. DVMRP is a protocol-specific multicast routing protocol, which means that it is designed to work with specific multicast protocols such as Internet Group Management Protocol (IGMP).
Connection Termination: Step 1: The client sends a FIN (finish) packet to the server, indicating that it wants to terminate the connection. Step 2: The server receives the FIN packet and sends an ACK packet back to the client, acknowledging the receipt of the FIN packet. Step 3: The server then sends its own FIN packet to the client, indicating that it also wants to terminate the connection. Step 4: The client receives the FIN packet and sends an ACK packet back to the server, acknowledging the receipt of the FIN packet. At this point, the connection is terminated.
Q2 Long Answer Questions.
a. List all the features of BGP. What are the three basic functions that BGP performs?
Border Gateway Protocol (BGP) is a routing protocol used to exchange routing information between different autonomous systems (AS) in the Internet. Some of the key features of BGP are:
Path vector protocol: BGP is a path vector protocol, which means it takes into account the AS path to reach a destination network.
Scalability: BGP is highly scalable and can handle a large number of routes in the Internet.
Policy-based routing: BGP allows network administrators to define routing policies based on various criteria such as AS path, community values, and route attributes.
Multi-homing: BGP supports multi-homing, which allows a network to connect to multiple ISPs for redundancy and load balancing.
Route filtering: BGP provides advanced filtering capabilities that allow network administrators to filter out unwanted routes.
Security: BGP provides security mechanisms such as MD5 authentication to prevent unauthorized access and spoofing attacks.
The three basic functions performed by BGP are:
Exchange of network reachability information: BGP routers exchange information about the networks they can reach and the preferred path to reach them.
Path selection: BGP routers use various criteria such as shortest AS path, local preference, and MED to select the best path to reach a destination network.
Policy enforcement: BGP routers enforce the routing policies defined by network administrators.
b. What is the basis of classification for the four types of links defined by Open Shortest Path First (OSPF)
Open Shortest Path First (OSPF) is a link-state routing protocol that is commonly used in enterprise networks. OSPF defines four types of links based on the speed and reliability of the link:
Point-to-point link: A point-to-point link is a dedicated link between two routers, and is typically the fastest and most reliable type of link.
Broadcast multi-access link: A broadcast multi-access link is a link that allows multiple routers to connect to the same network segment, such as an Ethernet LAN. This type of link is used to support OSPF neighbor relationships between routers on the same network segment.
Non-broadcast multi-access link: A non-broadcast multi-access link is similar to a broadcast multi-access link, but does not support broadcast or multicast traffic. This type of link is typically used in WAN environments.
Point-to-multipoint link: A point-to-multipoint link is a single link that connects a router to multiple other routers. This type of link is used in hub-and-spoke network topologies, where multiple routers connect to a central hub router.
Q3 Long Answer Questions.
a. Define Routing Information Protocol (RIP) message format.
Routing Information Protocol (RIP) is a distance-vector routing protocol that is used to exchange routing information between routers in a network. RIP message format consists of the following fields:
Command: This field indicates the type of RIP message, such as request, response, or update.
Version: This field specifies the version of RIP being used, either RIP-1 or RIP-2.
Address family identifier: This field indicates the type of IP address being used, either IPv4 or IPv6.
Route tag: This field is used to tag routes for policy enforcement or filtering.
IP address: This field specifies the destination network or the next-hop router address.
Subnet mask: This field specifies the network mask used for the destination network.
Next-hop router: This field specifies the address of the next-hop router for the destination network.
Metric: This field indicates the distance to the destination network, usually measured in hops.
b. Explain Error-Reporting messages in brief
Error-reporting messages are a type of network message used to indicate errors or problems in the network. Some common types of error-reporting messages are:
Destination unreachable: This message is generated by a router or host when it cannot reach the destination network or host. This can happen for various reasons such as an incorrect route or network outage.
Time exceeded: This message is generated by a router or host when a packet has exceeded the maximum time allowed for transmission in the network. This can happen when a packet is stuck in a routing loop or when a network is congested.
Parameter problem: This message is generated by a router or host when it encounters an invalid or unrecognized parameter in a network message. This can happen when a message is corrupted or when there is a misconfiguration in the network.
Redirect message: This message is generated by a router to inform a host that it should use a different next-hop router for a particular destination network. This can happen when a router discovers a shorter or more efficient path to a destination network.
Error-reporting messages are an important tool for network troubleshooting and can help identify and resolve network problems quickly.
Q4 Long Answer Questions.
a. With neat sketch explain connection establishment and connection termination using 3-way handshaking procedure in transport layer?
The 3-way handshaking procedure is used by the Transmission Control Protocol (TCP) to establish and terminate connections between two devices. The procedure consists of the following steps:
Connection Establishment:
Step 1: The client sends a SYN (synchronize) packet to the server. The packet contains the initial sequence number (ISN) that is used to synchronize the sequence numbers of the client and the server.
Step 2: The server receives the SYN packet and sends a SYN-ACK (synchronize-acknowledge) packet back to the client. The SYN-ACK packet contains an acknowledgment number that is used to acknowledge the receipt of the client's SYN packet, as well as the server's own ISN.
Step 3: The client receives the SYN-ACK packet and sends an ACK (acknowledge) packet to the server. The ACK packet contains the acknowledgment number of the SYN-ACK packet, as well as the next sequence number of the client. At this point, the connection is established and data can be exchanged between the client and the server.
Connection Termination: Step 1: The client sends a FIN (finish) packet to the server, indicating that it wants to terminate the connection. Step 2: The server receives the FIN packet and sends an ACK packet back to the client, acknowledging the receipt of the FIN packet. Step 3: The server then sends its own FIN packet to the client, indicating that it also wants to terminate the connection. Step 4: The client receives the FIN packet and sends an ACK packet back to the server, acknowledging the receipt of the FIN packet. At this point, the connection is terminated.
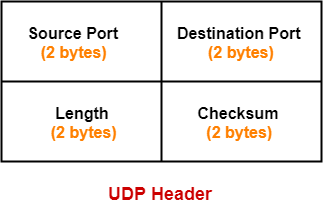
b. Draw the header of UDP. Explain all fields of UDP header.
User Datagram Protocol (UDP) is a connectionless transport protocol used for fast, low-overhead data transmission. The UDP header contains the following fields:
Destination port: This field identifies the port number used by the receiver.
Length: This field specifies the length of the UDP header and the data in bytes.
Checksum: This field is used for error detection and is optional in IPv4, but mandatory in IPv6.
The UDP header is relatively simple compared to other transport protocols such as TCP, as it does not include sequence numbers or acknowledgement numbers. Instead, UDP relies on the application layer to handle any necessary error detection and retransmission. Despite its simplicity, UDP is still widely used in applications such as video and audio streaming, DNS, and DHCP.
.jpg)
.jpg)



Comments
Post a Comment