Mobile Computing Unit 1 & 2
GGSIPU | B.TECH | 8th Semester | Mobile Computing | Unit 1 & 2
Unit 1
a) Explain wireless application protocols with the its version WAP 2.0 in detail.
Ref : https://www.javatpoint.com/wap
- WAP stands for Wireless Application Protocol, which is a standard protocol that allows the development and delivery of wireless content.
- It provides a complete end-to-end solution for mobile content delivery, including content creation, delivery, and presentation.
- WAP architecture consists of three main layers: Wireless Application Environment (WAE), Wireless Session Protocol (WSP), and Wireless Transport Layer Security (WTLS).
- The latest version of WAP is 2.0, which is an improvement over its previous versions and includes support for XHTML and improved security features.
- WAP 2.0 also includes the Push architecture, which allows applications to push data to a mobile device without any user intervention.
- The protocol uses HTTP as the underlying transport layer and supports various markup languages such as HTML, XHTML, and WML.
- WAP 2.0 also provides support for multimedia content, including images, audio, and video, and enables faster data transfer rates.
- The protocol is widely used for developing mobile web applications and is supported by various mobile devices and platforms.
b) Describe the working of a contention-based MAC protocol with suitable examples.
In a contention-based MAC protocol, nodes contend for the channel and attempt to transmit data. The protocol ensures fair access to the channel among the nodes without requiring any central control. The working of the protocol can be explained using the example of CSMA/CA protocol used in Wi-Fi networks. The protocol has two components: Carrier Sense: Before transmitting data, a node listens to the channel to check whether it is idle. If the channel is busy, the node waits for some time and then checks again. This process is known as carrier sense. Collision Avoidance: Once a node determines that the channel is idle, it sends data. However, other nodes may also have detected the channel as idle and may start transmitting at the same time, causing a collision. To avoid this, the transmitting node continues to monitor the channel while sending data and immediately stops transmission if it detects any other signal on the channel. The node then waits for some random time and tries again.
c) Discuss the functions of GPRS protocol stack with a diagram.
The GPRS protocol stack is divided into three layers: the application layer, the network layer, and the physical layer. Application layer: This layer is responsible for the user applications and their interaction with the network. It includes protocols such as WAP, HTTP, SMTP, and FTP. Network layer: This layer is responsible for routing packets through the network. It includes the following protocols: GTP (GPRS Tunneling Protocol): It is used to create tunnels between the SGSN and GGSN for transmitting user data. GPRS Mobility Management (GMM): It manages the mobility of mobile devices, including location updates and handovers. GPRS Session Management (GSM): It manages the setup, maintenance, and release of GPRS sessions. Physical layer: This layer is responsible for the transmission and reception of radio signals. It includes the following protocols: Radio Resource Management (RRM): It manages the allocation and management of radio resources. Logical Link Control (LLC): It provides a logical link between the mobile device and the network. Medium Access Control (MAC): It manages the access to the physical medium and is responsible for packet scheduling and transmission. Diagram:
[Mobile device] ⇔ [LLC] ⇔ [MAC] ⇔ [Physical Layer] ⇔ [Base Station] ⇔ [SGSN] ⇔ [GGSN] ⇔ [Internet] The mobile device communicates with the network via the physical layer, which is connected to a base station. The base station is connected to the SGSN (Serving GPRS Support Node), which is responsible for managing the mobile device's session and mobility. The SGSN is connected to the GGSN (Gateway GPRS Support Node), which is responsible for providing connectivity to the Internet. The LLC and MAC layers are responsible for managing the logical and physical links between the mobile device and the network.
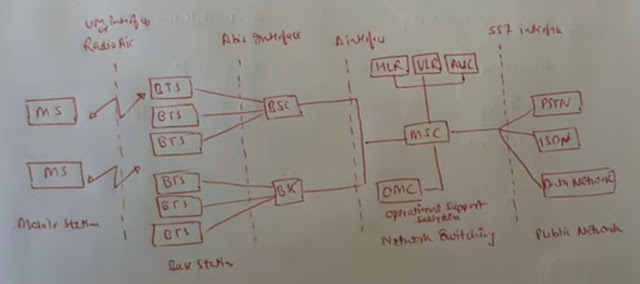
d) Describe GSM architecture and its service in detail. Explain about GSM authentication and security.
The GSM architecture consists of three subsystems:
- Base Station Subsystem (BSS)
- Network and Switching Subsystem (NSS)
- Operation and Support Subsystem (OSS)
Base Station Subsystem (BSS): BSS consists of the following components: Base Transceiver Station (BTS) Base Station Controller (BSC) Network and Switching Subsystem (NSS): NSS consists of the following components: Mobile Switching Center (MSC) Home Location Register (HLR) Visitor Location Register (VLR) Authentication Center (AUC) Equipment Identity Register (EIR) Operation and Support Subsystem (OSS): OSS consists of the following components: Operation and Maintenance Center (OMC) GSM Services: Voice Services Data Services Short Message Service (SMS) Supplementary Services GSM Authentication and Security:
- Subscriber Identity Module (SIM) stores the subscriber’s authentication information.
- Authentication is a process in which the SIM card verifies the identity of the subscriber to the network.
- After authentication, the network issues a temporary Mobile Subscriber Identity (TMSI) to the subscriber.
- If the subscriber is not registered with the network, the network will request the subscriber’s IMSI from the HLR.
- GSM uses A5 encryption algorithm to encrypt voice and data traffic over the air interface.
-
GSM also uses various security measures like Encryption, Authentication, and Integrity Protection to secure its network.
- Ref : https://youtu.be/v4PJET9ePuA
Unit 2
a) Explain the MAC layer in IEEE802.11. What are the fixed assignment schemes of MAC protocol? Explain their mechanism in detail.
The MAC (Media Access Control) layer in IEEE 802.11 standard defines the rules and procedures for sharing the wireless medium among multiple devices. It provides the framework for the exchange of data packets between the wireless nodes.
The IEEE 802.11 MAC protocol has two modes of operation: Distributed Coordination Function (DCF) and Point Coordination Function (PCF). DCF is the default mode of operation and is based on the CSMA/CA (Carrier Sense Multiple Access/Collision Avoidance) mechanism. In this mode, a device must wait for a fixed amount of time after sensing the wireless medium as busy before attempting to transmit data.
The fixed assignment schemes of the MAC protocol in IEEE 802.11 are as follows:
Time Division Multiple Access (TDMA): In this scheme, the wireless medium is divided into a series of time slots, and each device is assigned a unique time slot to transmit data. The TDMA scheme is used in situations where the bandwidth requirements of each device are known in advance.
Frequency Division Multiple Access (FDMA): In this scheme, the wireless medium is divided into a series of frequency channels, and each device is assigned a unique frequency channel to transmit data. The FDMA scheme is used in situations where the bandwidth requirements of each device are known in advance.
Code Division Multiple Access (CDMA): In this scheme, each device is assigned a unique code to transmit data. All devices transmit on the same frequency channel, but the receiver can differentiate between different devices based on their unique codes. The CDMA scheme is used in situations where the bandwidth requirements of each device are not known in advance.
The mechanism of the fixed assignment schemes is as follows:
TDMA: Each device is assigned a fixed time slot for data transmission. Devices must wait for their assigned time slot to transmit data. Time slots are allocated based on the required bandwidth of each device.
FDMA: Each device is assigned a fixed frequency channel for data transmission. Devices transmit data on their assigned frequency channel. Frequency channels are allocated based on the required bandwidth of each device.
CDMA: Each device is assigned a unique code for data transmission. Devices transmit data on the same frequency channel
b) Discuss the features of HiperLAN.
HiperLAN (High-Performance Radio Local Area Network) is a standard for wireless local area networks (WLANs) that operate in the 5 GHz frequency band. The features of HiperLAN are:
High Data Rates: HiperLAN provides high data transfer rates up to 54 Mbps.
Frequency Hopping Spread Spectrum (FHSS) Technology: HiperLAN uses FHSS technology for spreading the signal over a wide range of frequencies.
Support for Quality of Service (QoS): HiperLAN provides support for QoS, which allows the network to prioritize traffic based on its criticality and latency requirements.
Authentication and Encryption: HiperLAN provides secure communication through authentication and encryption mechanisms.
Error Correction: HiperLAN provides error correction mechanisms, which detect and correct any errors in the data transmitted over the network.
Dynamic Channel Selection: HiperLAN supports dynamic channel selection, which allows the network to automatically switch to a different channel in case of interference.
Multipath Fading: HiperLAN reduces the effect of multipath fading, which occurs when the signal bounces off walls and objects, by using techniques such as frequency diversity and time diversity.
Low Power Consumption: HiperLAN is designed to consume low power, making it suitable for battery-operated devices.
c) Explain the following:
a) WiMax technology and its applications
WiMAX (Worldwide Interoperability for Microwave Access) is a wireless communication standard that provides high-speed broadband connectivity over long distances. It operates on licensed and unlicensed frequencies, enabling it to be deployed in both urban and rural areas.
WiMAX offers several advantages over other wireless technologies, including high data rates, long-range coverage, and support for multiple users and quality of service (QoS). It can provide internet access to remote areas, and is also used in applications such as voice over IP (VoIP), multimedia streaming, and video conferencing.
b) ZigBee Technology and its usage.
ZigBee is a wireless communication protocol that is designed for low-power, low-data-rate applications. It operates on the IEEE 802.15.4 standard and is commonly used in applications such as home automation, building automation, and industrial automation.
ZigBee offers several advantages over other wireless technologies, including low power consumption, long battery life, and support for large networks with many devices. It also provides robust security features to ensure that data is transmitted securely. ZigBee is typically used in applications such as lighting control, temperature control, and energy management.





Comments
Post a Comment